
Free Internal Vulnerability Assessment (VA) & Report Delivered within HOURS, NOT Weeks
• Privacy assured: Your data never leaves your systems for the assessment.
• Zero Impact: as No scan, agent or software installation required.
• No Network or Firewall Reconfiguration needed.
• Perfect to verify the effectiveness of your existing VA solution.
• For organisations running Microsoft SCCM/ MECM.







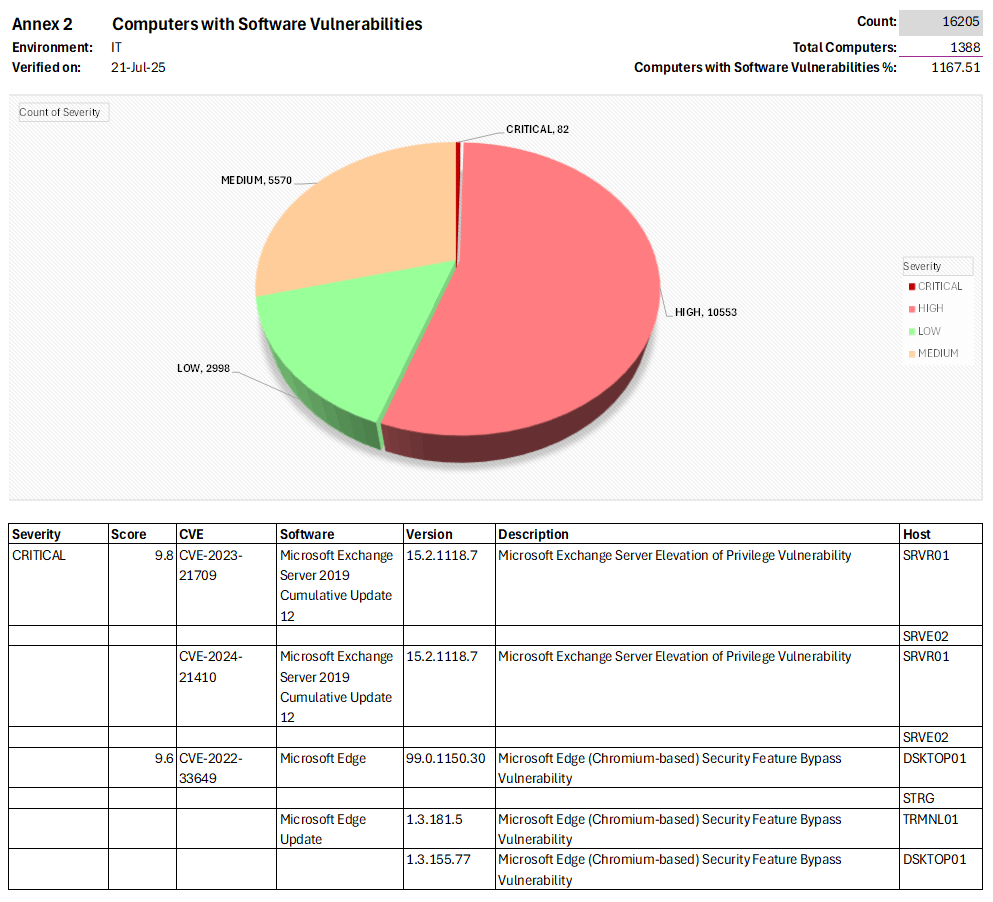
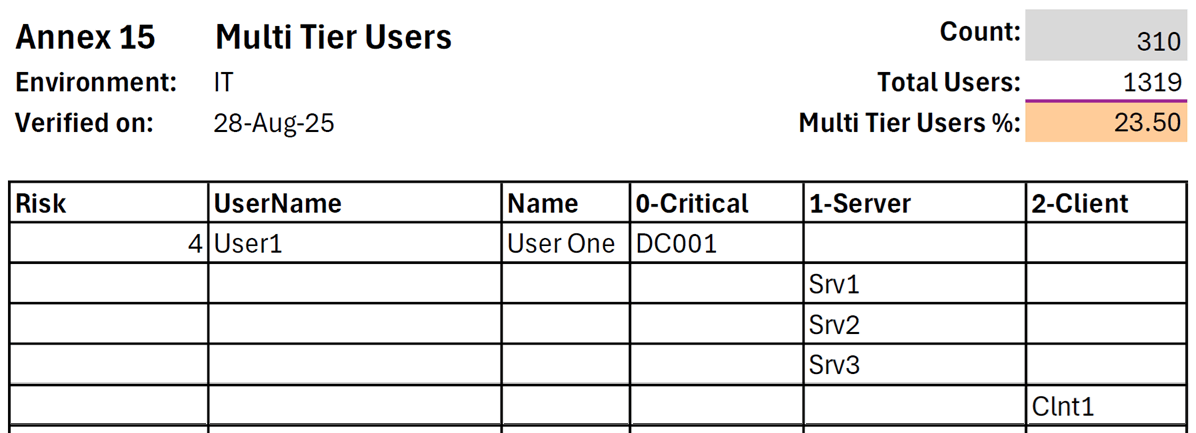
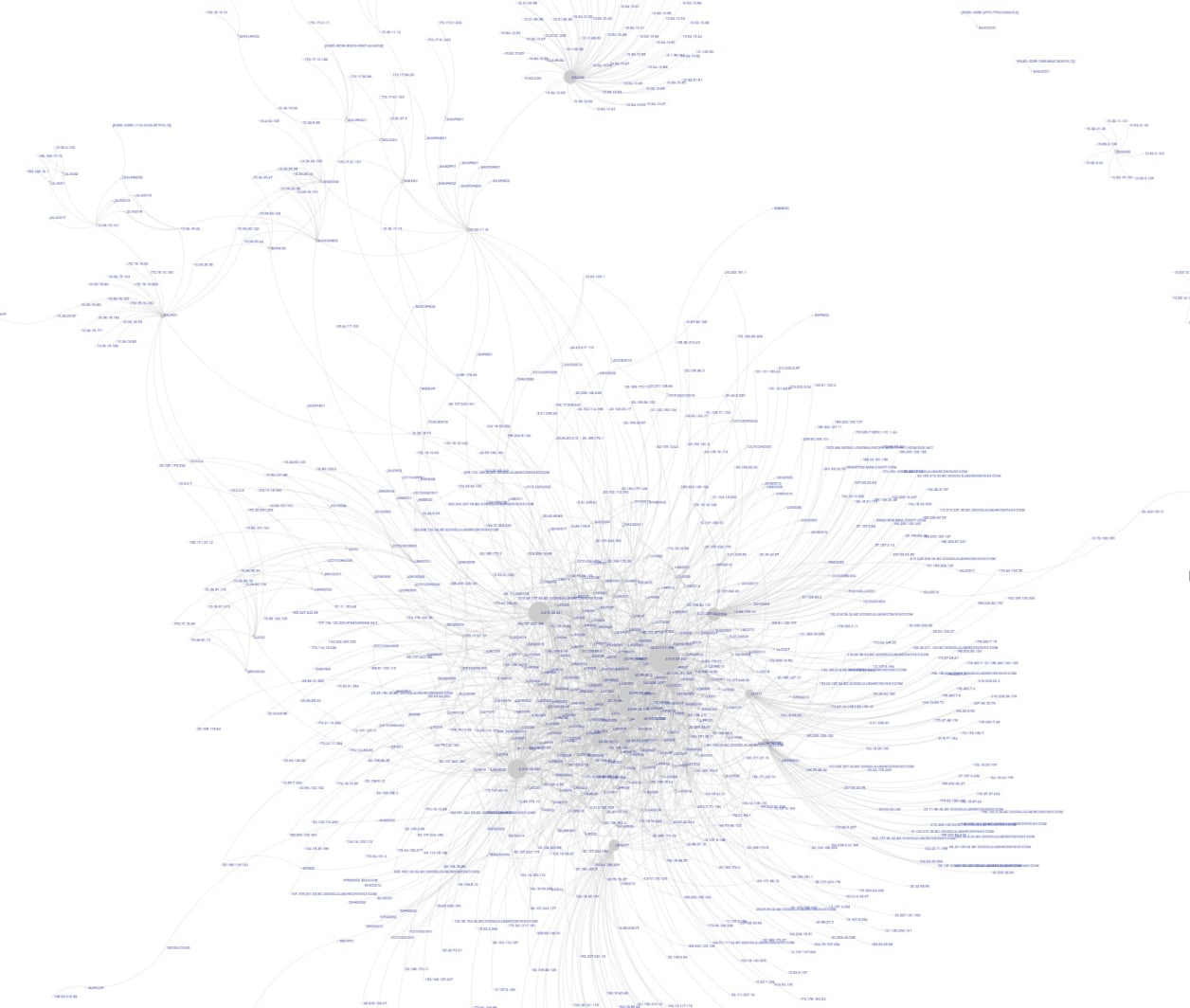

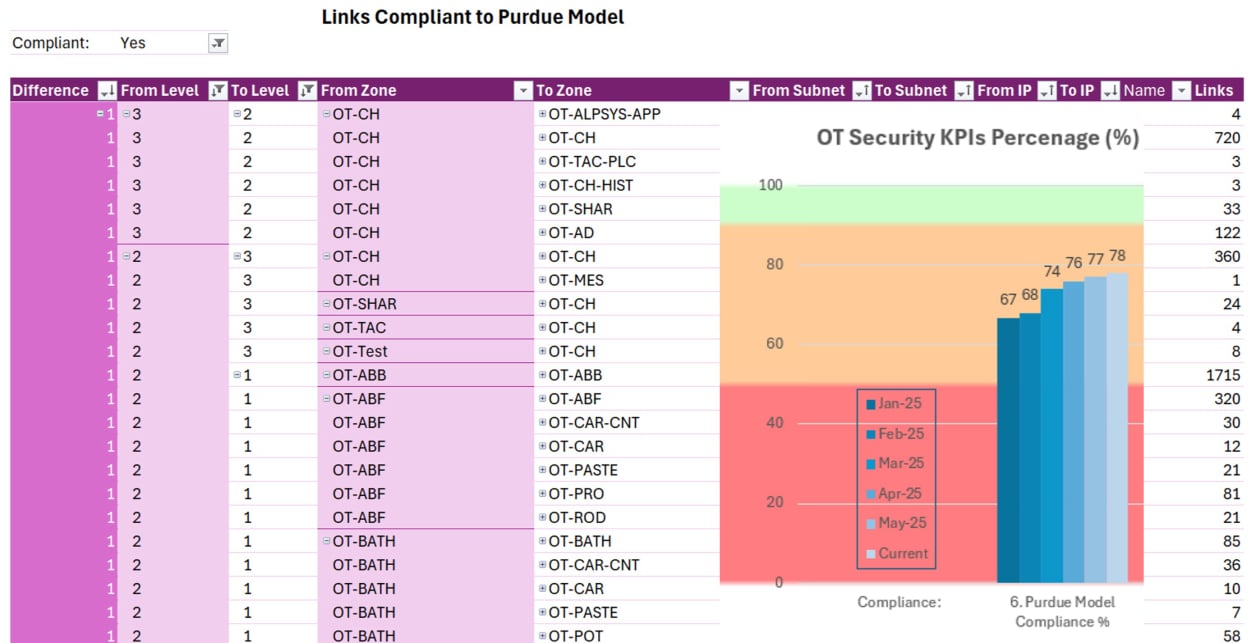



Contact us:
Email:
ping(a)secitics.com
LinkedIn:
SECITICS
WhatsApp:
+44 7707 381 530