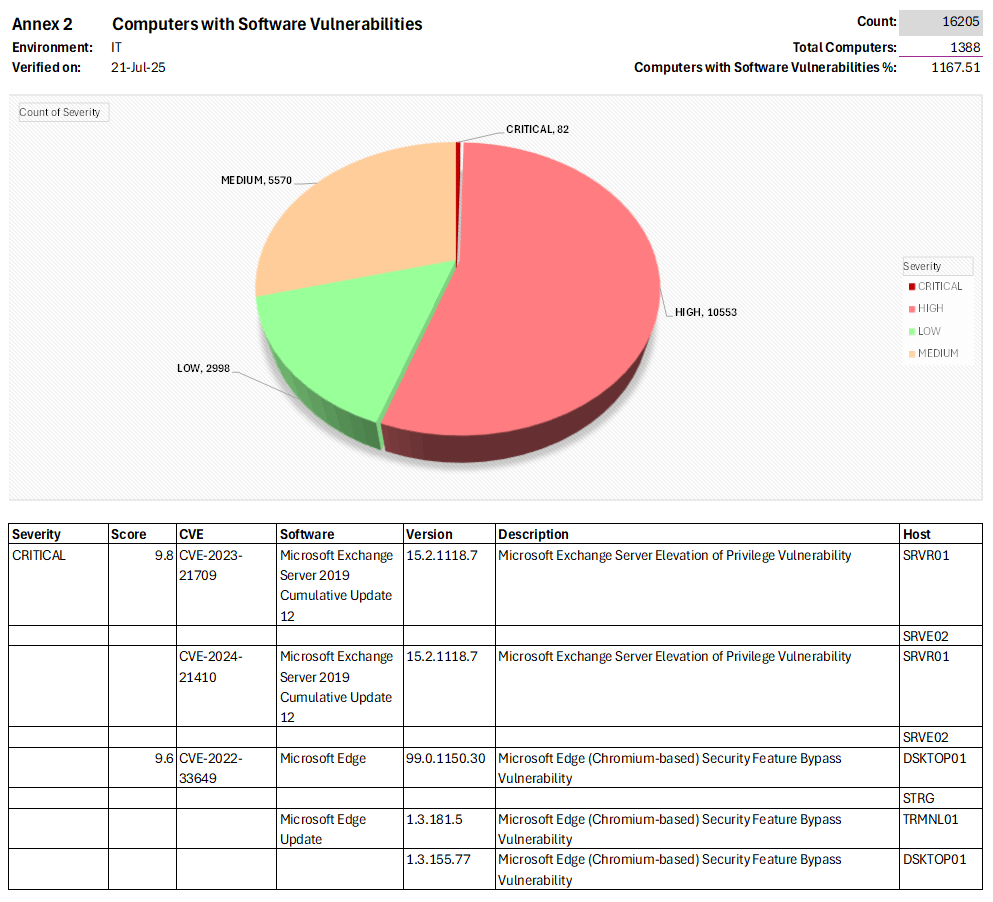
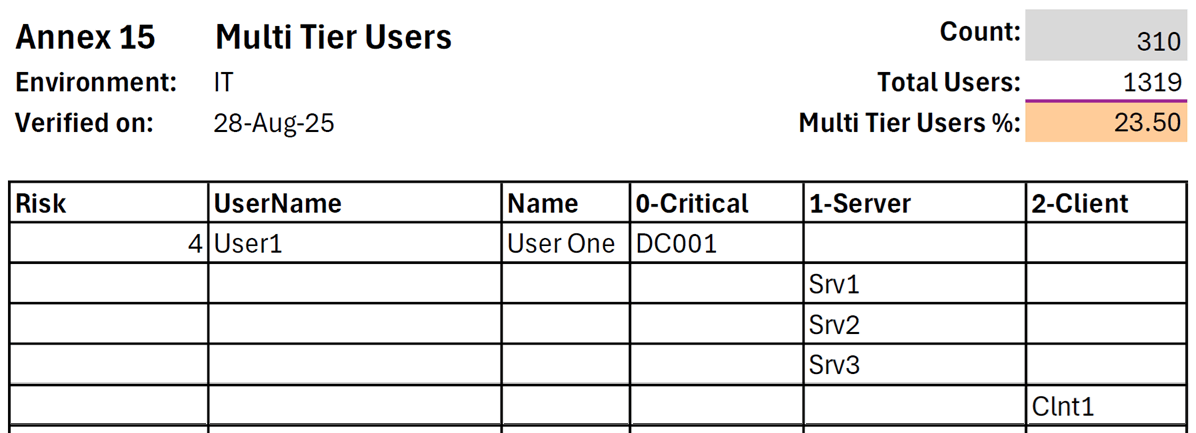
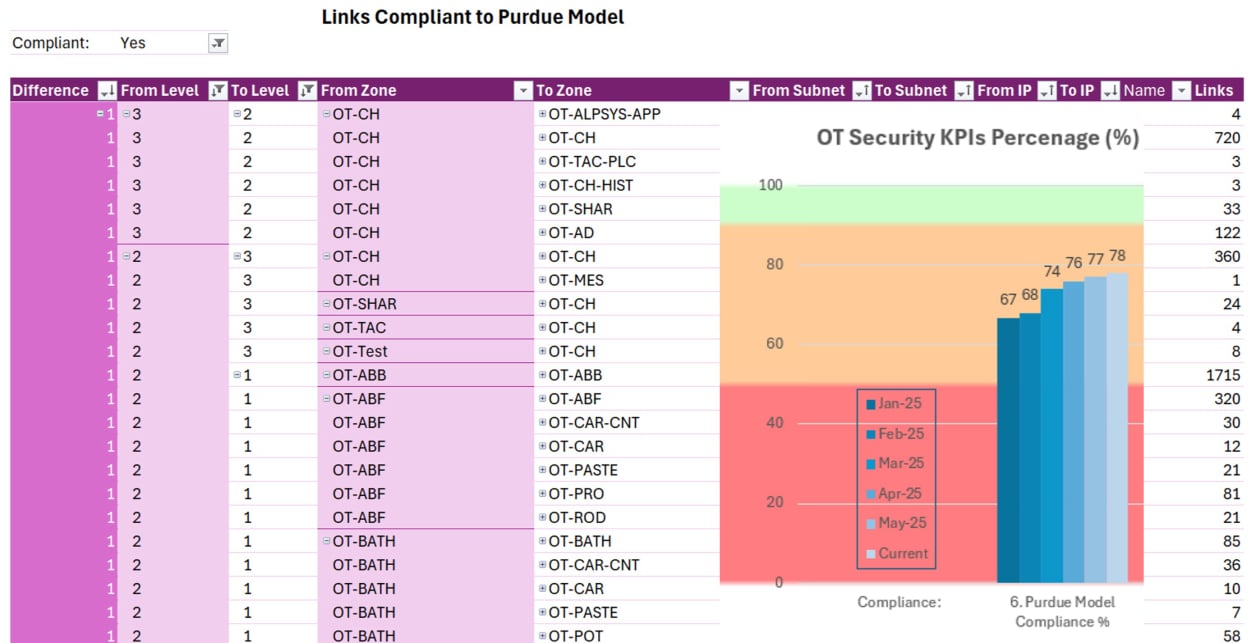
Vulnerability Visibility
• Visibility into Key Risk Indicators (KRIs) including severity ratings, prioritization scores, and vulnerability age.
• Actionable, recommended solutions for remediation and mitigations.
• Newly published vulnerabilities will be reported immediately, as the process does not rely on scanning dependency.


Contact us:
Email:
ping(a)secitics.com
LinkedIn:
SECITICS
WhatsApp:
+44 7707 381 530