Most Passive & Simplest Deployment
• Security starts with simplicity.
• No scan.
• No agent.
• No administrator user.

Most Passive & Simplest Deployment
• Security starts with simplicity.
• No scan.
• No agent.
• No administrator user.


Minimal Effort, Minimal Dependencies
• No appliance, or cabling required.
• No network switch port usage.
• No network switch reconfiguration.
• No load on network switch processor.
• No new firewall rules needed (in most cases).
• Typically requires as little as one VM.
• Designed for easy and flexible scalability.
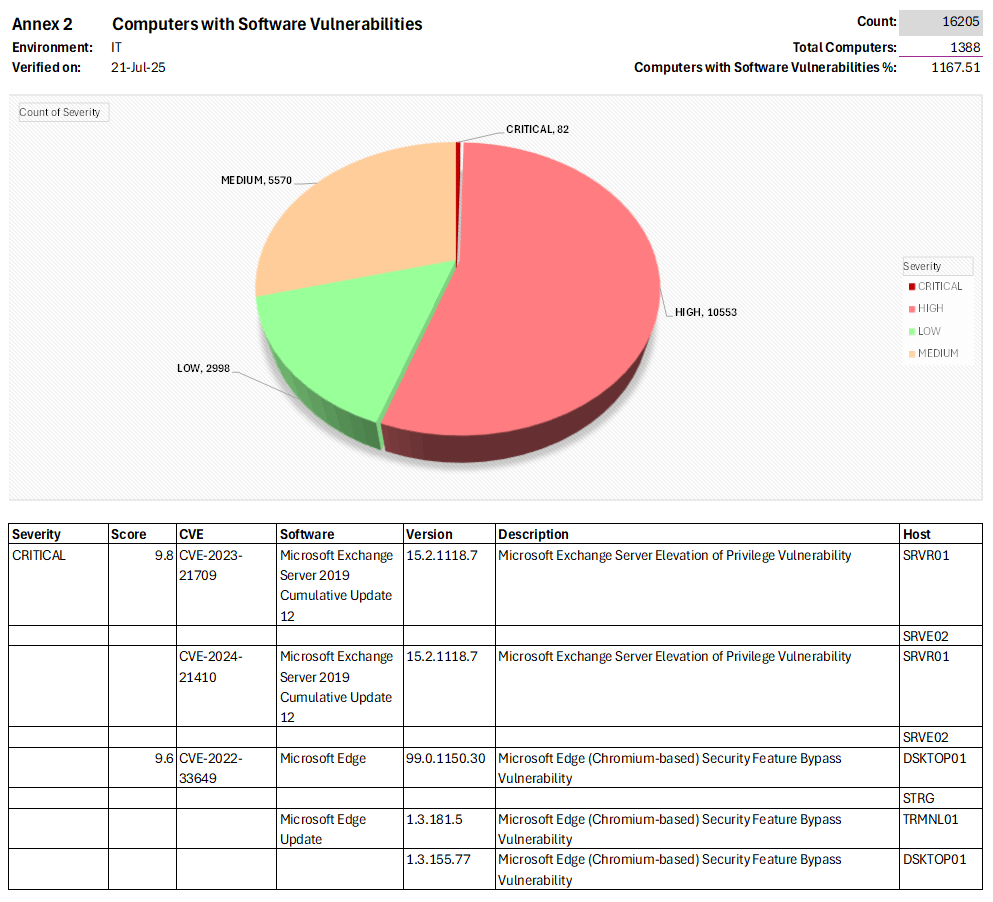
Vulnerability Visibility
• Visibility into Key Risk Indicators (KRIs) including severity ratings, prioritization scores, and vulnerability age.
• Actionable, recommended solutions for remediation and mitigations.
• Newly published vulnerabilities will be reported immediately, as the process does not rely on scanning dependency.
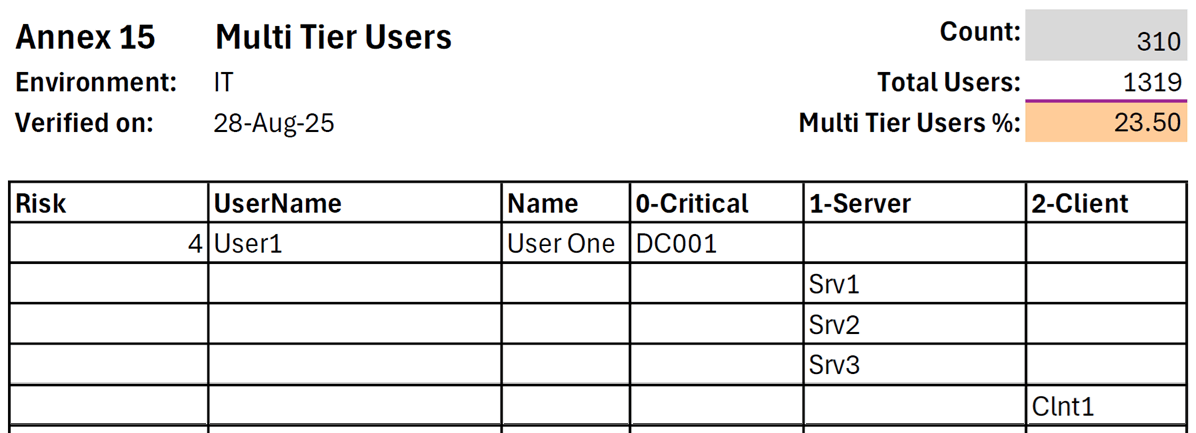
Enriching Identity of Human Assets
• User-centric vulnerabilities reports, including Hackmate attack paths to administrative accounts.
• Visibility into multi-tiered users .
Network Assets Visibility
• Detection and reporting of unmonitored assets.
• Ensuring zero blind spots.
• Detection of Rogue devices.
• Coverage for air-gapped segments and standalone systems.
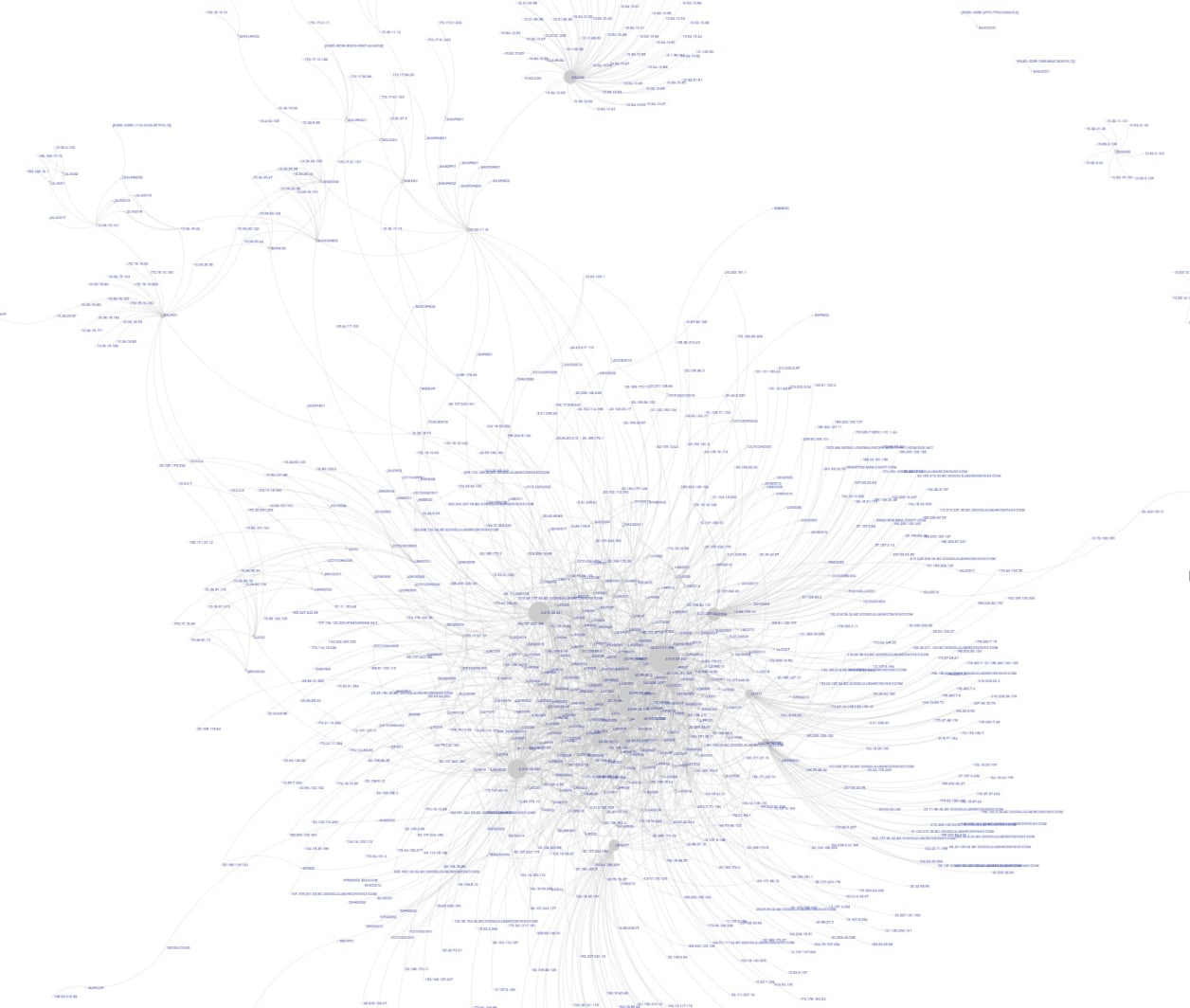
AI-Powered Full-Spectrum Visibility into IT & ICS/OT/CPS Assets
• Graph of network connections within the same level/zone as well as across different levels/zones.
• Visual representation of IEC 62443 / Purdue model level compliance.

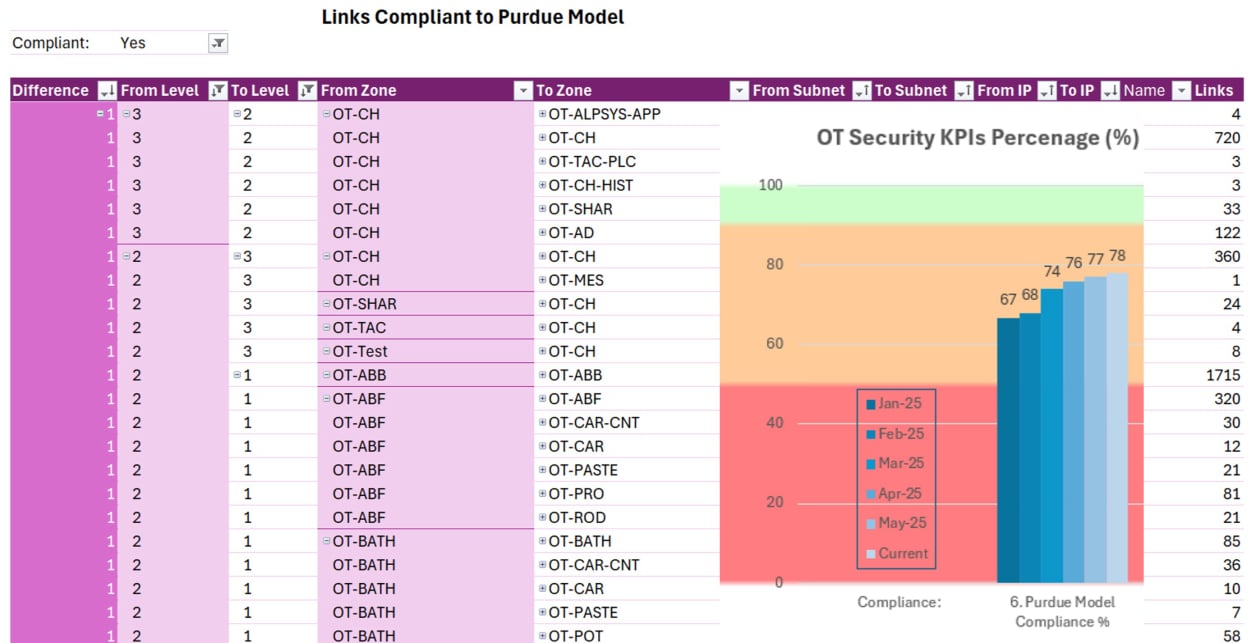
IEC 62443 / Purdue Model Compliance Report
• Identification of compliant and non-compliant links.
• Trend analysis of compliance percentage over time.
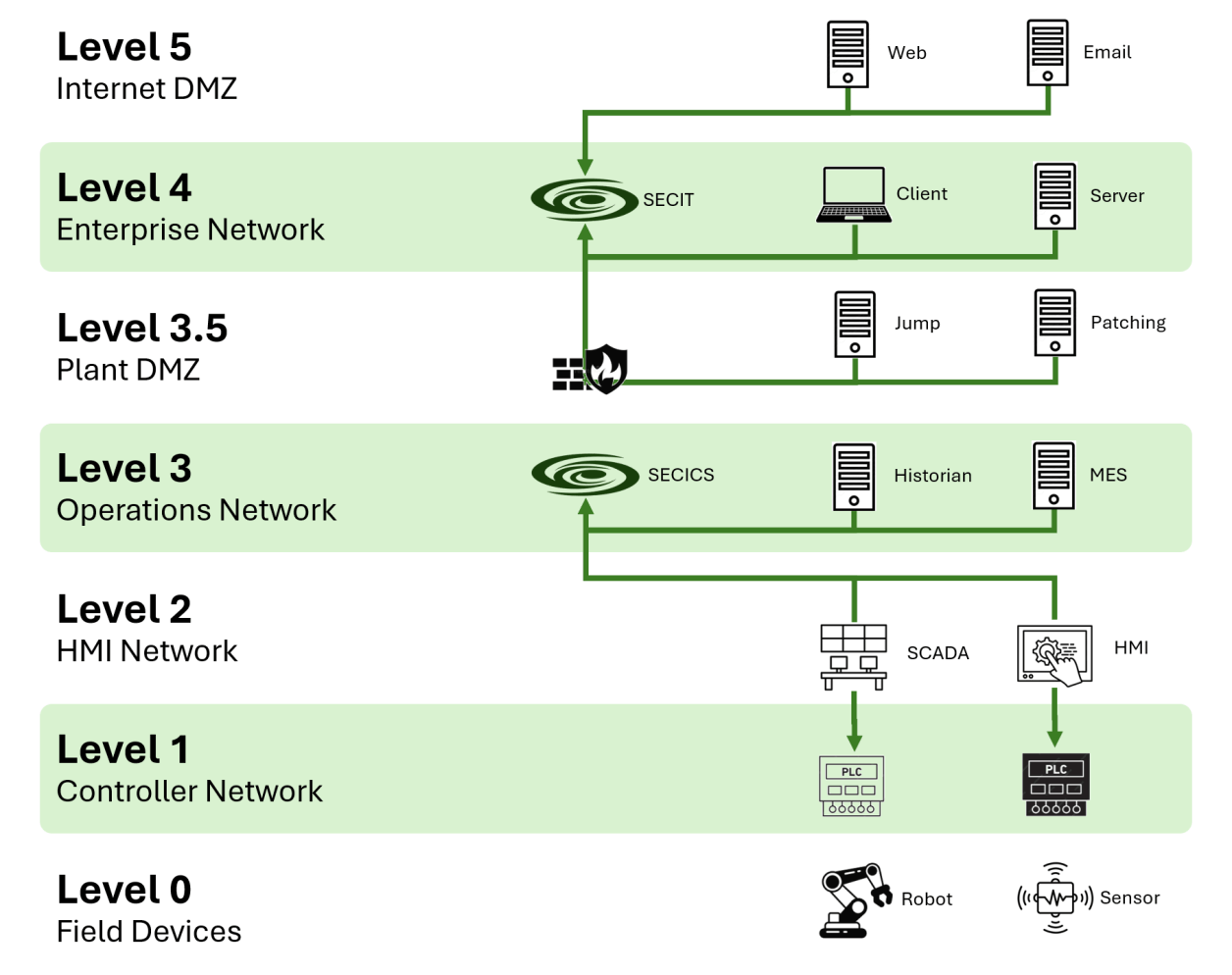
Maximum Compliant to Intel. & regional Cyber Security and ICS Security Standards:
OTCC - OT Cybersecurity Controls
NIAF - National Info. Assurance Framework
DESC - ICS Security Standard
NIA - National Info. Assurance Policy
QCSF
IEC 62443
No Purdue level bypassing
No inbound traffic (new)
Secured by:
HTML Website Builder
Contact us:
Email:
ping(a)secitics.com
LinkedIn:
SECITICS
WhatsApp:
+44 7707 381 530